File Transfer Protocol presents an enigma to users of the IBM i OS. It can be used to easily and quickly transfer objects between systems including program updates and data. It doesn’t need command line access so a remote user can manipulate objects directly. It is also a potential weakness that could open up your system to malicious access. Within an FTP session, a command line of sorts is available and FTP commands can be issued to retrieve objects, send objects, list objects, call programs, run commands and even delete objects from your system.
With all this utility enabled, it presents a security nightmare. If FTP is not secured, a compromised user profile and password could yield catastrophic results.
If you are using FTP, then you must consider the security ramifications. A best practice for securing FTP is to implement exit point controls. If that isn’t possible, then the IBM i OS includes a feature called Function Usage that will let you control FTP. Function Usage controls who is allowed to connect with your system using FTP from a remote location, what FTP commands they are allowed to use and who can initiate an FTP session from your IBM i to a remote server. As shipped from IBM, FTP Function Usage settings are all set to allow anyone to use FTP in any way.
To review the FTP controls using Function Usage, use the following command:
WRKFCNUSG FCNID(QIBM_QT*)
This will show you all of the functions defined for FTP.
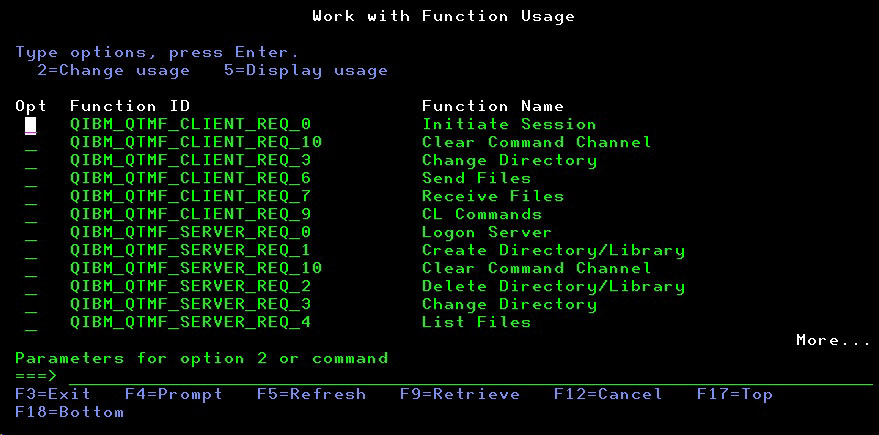
The “CLIENT” functions apply to FTP initiated from your IBM i system and the “SERVER” functions apply to remote FTP sessions connecting in to your system. To see how your system is configured for users establishing a remote connection into your system, put a 5 next to the function marked QIBM_QTMF_SERVER_REQ_0.
The following will be shown:
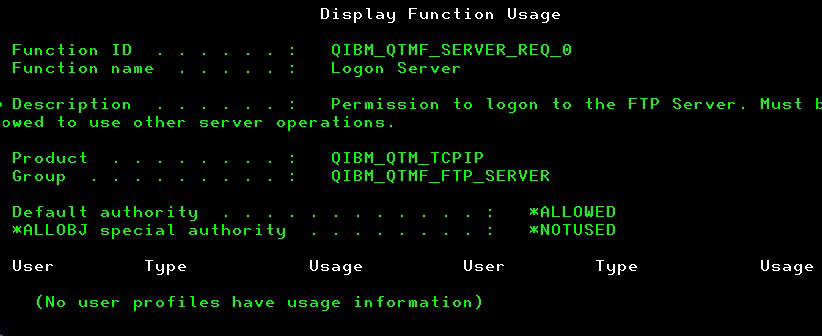
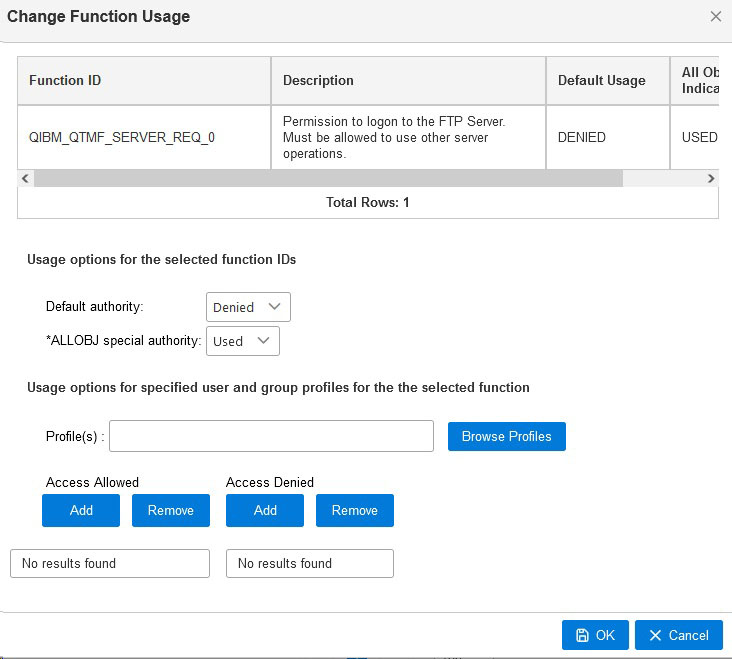
As shown here, anyone is allowed to connect to your system as long as the FTP server function is up and running. To deny any use of the FTP Server on your system, just use option 2 and change the “Default authority” to *DENIED. At this point, no FTP session can be established.
To authorize one or more specific user profiles, use option 2 and enter the user profile with usage setting *ALLOWED. Important note: When making changes using option 2, the “Default authority” setting will try to reset to *ALLOWED and you will have to re-enter the *DENIED setting if that is what you want. When you have it updated, the function setting might look like this:
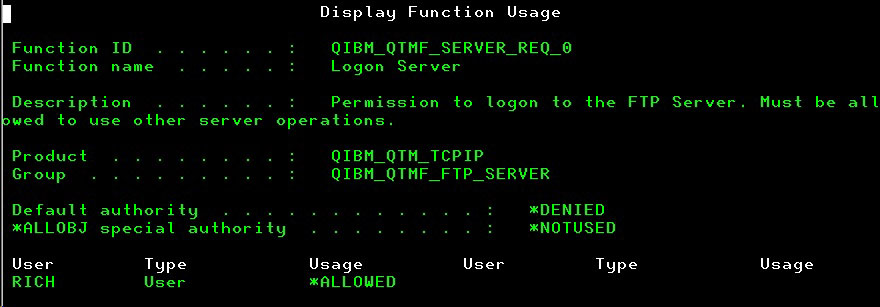
In this case, the only user profile allowed access for remote FTP is RICH.
Another option for you to consider is that you can set the function to only allow user profiles with *ALLOBJ authority. That way, with just a single update, you can allow access to trusted users. Be careful when taking this option since a lot of IBM i OS shops have users granted too much authority.
When making changes to the way the function is configured, you do not need to end and restart the FTP server.
To control which users can start an FTP connect to a remote server, use the function QIBM_QTMF_CLIENT_REQ_0. The same method as described above can be used to control the function.
The other functions let you control the granularity of how FTP sessions are used. We recommend that you explore these in detail to gain the level of security that you are comfortable with.
Function Usage can also be configured using IBM i Navigator. After signing on, look for this link:
You may need to scroll down quite a way to see the FTP functions. Or, you can enter QIBM_QTMF in the filter field:
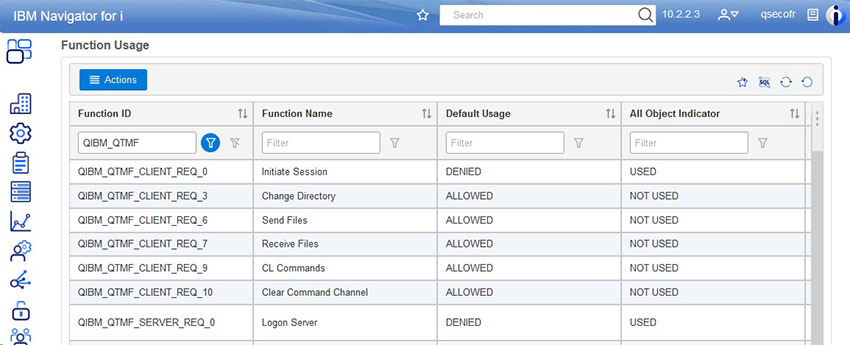
Right click on the function you want to work with and select “Change”.
For full logging and alerting of FTP, take a look at our SafeNet/i product.
Our security audit software, iSecMap reports on changes in Function Usage configuration.